We know everyone is busy. Everyone already has too much on their plate and is trying to learn as much as they can every day.
But here, in a nutshell, is what you can teach yourself, your co-workers, your friends, and your family to help them to better recognize and beat social engineering and phishing. It’s not perfect. It doesn’t cover every scenario, but it does cover a huge percentage of them. And if you learn and teach it well…if you make a culture of healthy skepticism around these common social engineering/phishing traits, nothing else you could learn or teach will reduce more risk.
KnowBe4 has been teaching the same lesson since the very beginning: Stop! Look! Think!
It’s the guiding message of all content that the security awareness training platform delivers.
Teach two common traits of all social engineering and recommend one response. What could be easier to teach and create a culture around?
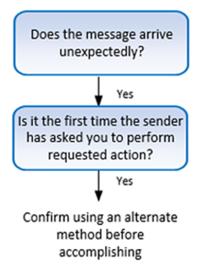
If any message (be it in an email, website, social media, SMS text, or voice call), arrives unexpectedly and the sender, no matter who it first appears to be, is asking you to perform a new action for the first time, realize that this is a higher risk message than all the others. Most social engineering scams begin this way.
You may or may not recognize the sender. It really doesn’t matter. The sender’s email address can be faked, or it can even be the sender’s real account which has been hacked and used by a scammer. So, notice that the flow chart doesn’t include the oft repeated suggestion, “Do you recognize the sender?” It’s not a bad trait to care about, but it just means less these days as hackers are so frequently taking over people’s legitimate accounts. Who among us hasn’t gotten a phishing message in social media from a trusted friend’s account that has been taken over?
Most social engineering scams arrive unexpectedly. We were not waiting for the message or the call. It just came to us. It was in our inbox or via an inbound voice call, and suddenly someone was asking us to do something, for them, that we’ve never done before. The request may even sound plausible. In fact, most social engineering scams contain plausible requests…to check on so and so, download this document, provide this necessary piece of information, and so on. If social engineering scams didn’t ask for plausible actions, no one would ever fall for the scams. Most are asking for things that seem normal for the scenario they are claiming.
So, the trait to watch out for is the requestor, whoever they are, are asking you to do something unique for them that you’ve never done for that person or organization before. It can even be something you’ve done before…just not for that requestor.
Yes, many legitimate requests have both traits: arrive unexpectedly and ask you to do something new.
But the key is to recognize that these are also very common signs of social engineering scams. It may not be that the unexpected request is a scam. Just train yourself that whenever you see these two things, that you slow down and confirm using an alternate trusted method (e.g., call the person on a known good phone number, go directly to the vendor’s known good website URL instead of clicking on the link in the email, etc.).
There are other common traits of social engineering scams, such as the request contains a “stressor event” where they are trying to get you to make a quick decision…because you’ll lose access to a trusted account, lose money, lose a business deal, make someone mad, etc. and any message including a stressor event adds to the suspicion.
But let’s start with two easy conditions that anyone can learn to lookout for and how to respond. Quick and easy. Not much to remember. But so much power in learning to create a culture and healthy level of default skepticism around any message with these two traits. Really, it’s the most important cybersecurity lesson and defense you can teach. Nothing would reduce more risk.
Stop! Look! Think!