Distributed denial-of-service (DDoS) attacks continued to surge throughout 2023, indicating a 16% overall increase globally compared to the previous year. A fresh Zayo report, based on data collected from its DDoS customers, found the telecom industry was hit especially hard.
DDoS is an attack where the target’s internet circuit is flooded with false or unauthorized traffic, obstructing legitimate user traffic from flowing through. These cyberattacks are evolving, becoming more sophisticated, automated and elusive, making detection increasingly difficult.
In the second quarter Zayo saw a staggering 387% increase in DDoS attacks compared to the first. The volume of attacks was magnitudes higher than the previous, and following quarters, due to several factors including the upswing in for-hire botnet usage, a pro-Russia DDoS hacker group formed in March and the emergence of more multi-vector attacks.
DDoS activity leveled in the second half of the year. But the bad news is attack volume is still ticking up quickly. Since early 2021, there has been a 150% increase in DDoS attacks globally. Some industry estimates say there are around 23,000 DDoS attacks every day globally, while others claim there are over 40,000. According to Zayo, they are more common than phishing, spoofing, insider threats and DNS tunneling attacks.
Telecom targeted
The telecom sector bore the brunt of DDoS attacks in 2023, emerging as a primary target for threat actors seeking to disrupt critical communication infrastructure. Industry experts have warned telcos that new strategies are needed to confront the growing threat landscape.
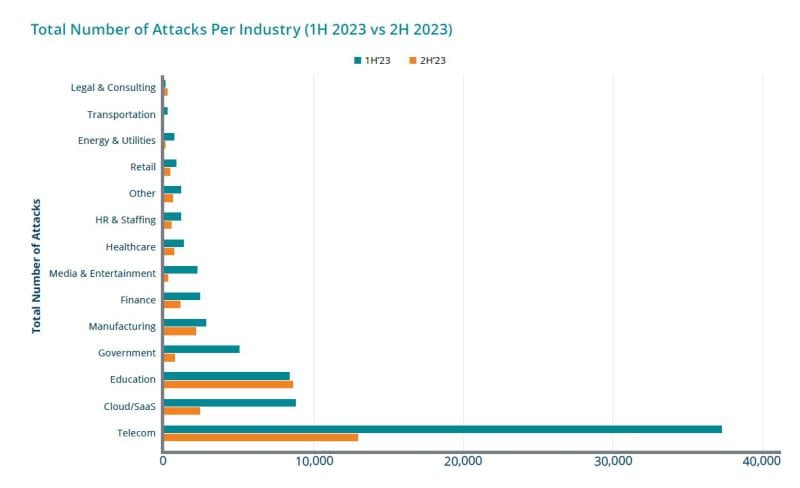
The devastating second quarter across all industries was especially bad for telecom. Zayo's report revealed the telecom industry's susceptibility to DDoS assaults, with companies enduring the most frequent attacks throughout 2023. In the first half of the year, telecom companies weathered approximately 37,000 attacks, comprising half of the total attack volume. This trend persisted in the latter half, with telecom companies facing nearly 13,000 attacks, accounting for 40% of the total volume.
Why telecom? Zayo said there are a few factors, one being the prize of sensitive information belonging to millions of users. Also, telecom presents attackers with the possibility of disrupting communication for political purposes and the “vast attack surface of their (often outdated) digital assets” can be seen as low-hanging fruit.
Data from Lumen showed the largest assault of 2023 occurring in Q4, peaking at 903 Gbps, which targeted a telecom customer.
Gov’t hit with the longest attacks
The government sector also faced a surge of DDoS attacks in Q4, as revealed by Lumen Technologies' latest report. Analysis of data from its DDoS mitigation platform unveiled the severity of those attacks.
Notably, 66% of the 1,000 largest DDoS attacks mitigated by Lumen targeted government entities, marking a 163% increase from Q3 and a staggering 4,025% surge year over year. One unnamed government customer bore the brunt of 1,759 attacks out of 1,953 government-targeted assaults in the fourth quarter.
Sharada Achanta, Lumen's VP of Product, Cybersecurity, and AI, emphasized the government sector's vulnerability due to its possession of sensitive data, making it an enticing target for cyberattacks driven by espionage, extortion and disruption motives.
Zayo's data revealed the government is often facing the most prolonged attacks as well, with average attack durations escalating from 4 hours in the first half of 2023 to nearly 18 hours in the latter half, representing a 322% increase. With the 2024 presidential election looming, Zayo noted federal, state and local government institutions will likely face ongoing battles against sustained assaults.
New DDoS attack strategies and AI
The cybersecurity landscape is evolving rapidly, with attackers increasingly relying on bot-based strategies for more sustained DDoS assaults. This “paradigm shift,” said Zayo, underscores the evolving nature and scope of DDoS threats, posing a growing challenge to organizations across all industries.
In the second half of 2023, short burst attacks – those lasting less than 10 minutes – still represented the majority of attacks (over 72%). However, this percentage decreased from the first half of the year, when 83% of attacks were under 10 minutes in length, representing "a worrying trend." As frequency has dropped, attacks are lasting much longer. The data from Zayo shows that the average DDoS attack in 2023 lasted 68 minutes.
Across all industries, the overall size of DDoS attacks detected by Zayo fell from the first half to the second half of 2023. Zayo said the decrease in attack size in late 2023 could indicate another troubling trend: the emergence of multi-vector attacks. These sophisticated attacks combine various tactics including carpet-bombing, DNS flood attacks, TCP and HTTP/HTTPS attacks, to maximize disruption and evade detection.
Lumen's report pointed out the dual role of artificial intelligence (AI) in new cybersecurity use cases, serving as both a weapon for attackers and a shield for defenders. Integrating AI for security at the network edge (IoT devices, smartphones, and laptops) raises concerns about AI-driven attacks, including DDoS assaults employing compromised IoT devices and deepfake attacks utilizing manipulated audio and video.
Regardless of attack frequency, duration, or size, unprotected organizations face significant costs, with Zayo estimating an average of $6,000 per minute during a DDoS attack. These costs encompass lost revenue, detection and recovery expenses, legal fees, reputational harm and customer churn, among others. Zayo said those factors can cause costs to “easily surpass $150,000 for a single 20-minute attack.”
Nonetheless, DDoS protection “has largely kept pace” with attack volume, evolving to be able to protect organizations against attacks. Zayo announced its own DDoS protection in 2022, and Lumen, Nokia, NetScout and Arrcus have also announced products that include DDoS prevention in response to growing threats.
